 |
Enterprise-wide Security Management |
 |
Enterprise-wide Security Management |
| Rule
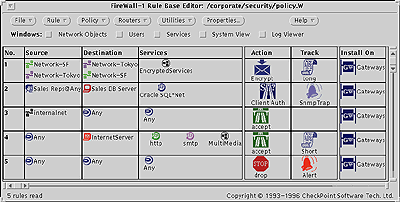
Base Editor. FireWall-1's award-winning graphical user interface makes it easy to build an enterprise-wide security policy. Object-oriented technology simplifies the definition process and the editor checks automatically for rule base consistency. |
Based on an intuitive, award-winning graphical user
interface, FireWall-1 offers a powerful set of
graphical tools for easy definition of the security
policy, flexible management, auditing, reporting and
seamless departmental integration of enterprise-wide
security. Ease of Use FireWall-1 was designed to be easily installed, configured and managed. Based upon object-oriented technology, the graphical user interface makes it easy to group entities for more efficient control and allows for new security policies to be implemented or existing policies to be modified without interrupting system operation. Once a security policy is defined, it is automatically checked for consistency to ensure that rules within the policy do not conflict, ensuring a high degree of integrity and reducing the potential for operator error. Centralized Control With FireWall-1, organizations can configure and manage an enterprise-wide security policy across multiple gateways and multiple servers from a single, centralized workstation. This eliminates the need to configure each gateway and server independently. The system administrator simply defines a single security policy for the enterprise which is then automatically distributed to each gateway. All communication between the management module and the firewall modules is authenticated and digitally signed for added security. |
 |
Real-time Alerting FireWall-1's alerting capabilities allow for real-time notification of any suspicious activity. Alerts can generate a notification for the system manager, send an e-mail message, send an SNMP alert to another network management system, or activate any user-defined alert (e.g. triggering an application that calls the system manager's pager). Using the Rule Base, different alert types can be assigned to different network traffic patterns. The powerful system viewer displays, in one window, the activity of each security gateway distributed throughout the enterprise. Graphical icons show each gateway's operational status and statistical counters track the number of packets inspected, rejected and logged. |
[Back] [Home] [Next]
[1] [2] [3] [4] [5] [6] [7] [8] [9] [10] [11] [12]